- Email: info@craw.sg
- Phone: +65 9797 6564

Let’s talk about the Application Penetration Testing Services and explore the uses of these services for the protection of organizations working in the IT Industry! Here, we will talk about the techniques that are used in application penetration testing.
In the end, we will introduce you to a VAPT service provider offering the best experience for application penetration testing services. What are we waiting for? Let’s get started!

Professional services called application penetration testing are provided by cybersecurity companies to assist businesses in identifying and addressing security flaws in their apps. In order to find and take advantage of vulnerabilities, these services use ethical hackers to mimic a real-world strike.
Before malevolent attackers cause a breach, the objective is to deliver a thorough assessment of an application’s security posture along with practical remedy recommendations. Let’s explore Application Penetration Testing Services!
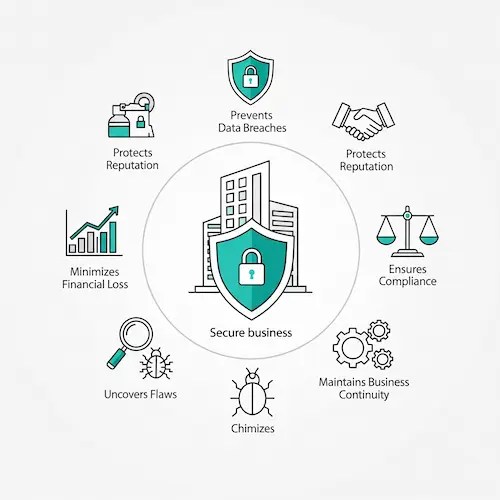
Application Penetration Testing is essential for your business for the following reasons:
1. Prevents Data Breaches: By proactively identifying and addressing vulnerabilities that attackers might exploit, penetration testing helps to avoid expensive and harmful data breaches.
2. Protects Brand Reputation and Customer Trust: Penetration testing preserves a positive company image and client confidence by showcasing a dedication to security and preventing breaches.
3. Ensures Regulatory and Industry Compliance: Regular penetration testing is required by numerous laws, including PCI DSS, HIPAA, and GDPR, and is therefore essential to avoiding fines and penalties.
4. Minimizes Financial Loss: Finding and fixing vulnerabilities proactively using a test is significantly less expensive than dealing with the financial consequences of a breach, which include lost revenue, legal fees, and remediation costs.
5. Validates Security Investments: Pen testing offers a practical evaluation of how well your current security measures, like firewalls and encryption, are safeguarding your application.
6. Uncovers Flaws Automated Scanners Miss: Expert human testers can spot intricate problems that automated tools miss, such as chained attack routes and business logic vulnerabilities.
7. Improves Security Awareness and Practices: Test results give development and security teams useful training that helps them comprehend and use stronger security procedures in the future.
8. Maintains Business Continuity: Penetration testing helps guarantee that your business operations can continue without interruption from a cyberattack by detecting and reducing threats to vital applications.
| S.No. | Roles | What? |
| 1. | Simulating Realistic Attacks | To mimic actual cyberattacks on a system, network, or application, professional penetration testers take on the role of ethical hackers. |
| 2. | Identifying and Exploiting Vulnerabilities | They find and then take advantage of security vulnerabilities, like configuration errors or weak code, using a mix of automated tools and manual methods. |
| 3. | Assessing Risk and Business Impact | By showing what sensitive data they can access or what systems they may corrupt, testers assess the possible harm and business impact of a successful breach. |
| 4. | Providing Actionable Recommendations | They produce a thorough report that lists all of the vulnerabilities discovered and gives developers and IT teams specific, prioritized instructions on how to address them. |
| 5. | Validating Security Controls | Penetration testers confirm that intrusion detection systems and firewalls, among other security measures, are resilient to specific attacks and are operating efficiently. |
| 6. | Ensuring Compliance | Through the provision of the required documents to demonstrate security due diligence, their work assists firms in meeting industry and regulatory standards, including PCI DSS and HIPAA. |
| 7. | Improving Overall Security Posture | Penetration testers help a business develop its security procedures and create more robust systems over time by continuously identifying and assisting in the correction of vulnerabilities. |
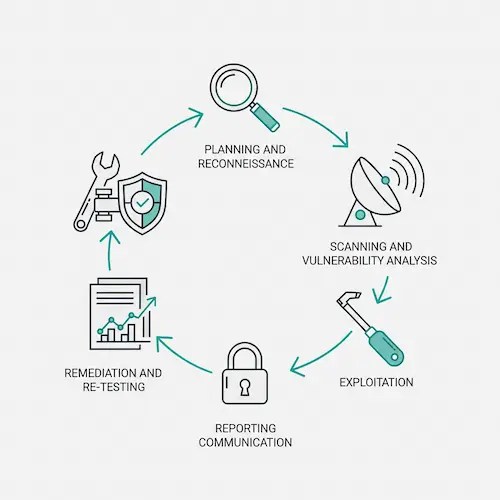
The following is the penetration testing process:
| S.No. | Benefits | What? |
| 1. | Human Expertise for Complex Threats | Expert testers identify intricate flaws in business logic and chained attack vectors that automated tools overlook by applying their expertise and inventiveness. |
| 2. | Realistic Attack Simulation | They show the practical effects of a successful breach by simulating an attacker’s mental process in a realistic manner. |
| 3. | Comprehensive Risk Assessment | Experts help you prioritize what needs to be corrected first by identifying vulnerabilities and evaluating the possible harm and financial impact. |
| 4. | Actionable and Tailored Recommendations | Their bespoke reports provide precise, measurable, and doable actions for your security and development teams to take to fix the problems. |
| 5. | Validation of Security Controls | They assess the effectiveness of your current security measures, such as intrusion detection systems and firewalls, in fending off a deliberate attack. |
| 6. | Ensuring Compliance | Employing professionals gives you the paperwork you need to demonstrate due diligence and helps you comply with stringent industry and regulatory requirements like PCI DSS and HIPAA. |
| 7. | Protection of Brand Reputation | By proactively detecting and addressing security vulnerabilities, you may avoid breaches, protect your business’s brand, and keep customers’ trust. |
| 8. | Improving Security Posture | Over time, their advice and insights assist your company in developing more robust apps and advancing its security procedures. |

Professional application penetration testing improves your security in the following ways:
| S.No. | Factors | Topics | What? |
| 1. | Methodology | Penetration Testing | An ethical hacker’s manual, hands-on procedure is called a penetration test. It entails deliberately exploiting weaknesses by combining automated technologies with human skills. |
| Vulnerability Scanning | An automated procedure called vulnerability scanning compares a system or network to a database of known vulnerabilities using software. | ||
| 2. | Purpose | Penetration Testing | To find out whether a system can be compromised, how far an attacker may go, and what the possible commercial impact might be, the objective is to mimic a real-world cyberattack. |
| Vulnerability Scanning | Finding and reporting known security flaws, such as unpatched software, incorrect setups, and obsolete components, is the aim. | ||
| 3. | Scope | Penetration Testing | To conduct a thorough, in-depth study, the scope is usually limited and concentrated on particular goals, such as a single application. |
| Vulnerability Scanning | Usually broad, the scope is intended to give a comprehensive picture of an organization’s whole network or infrastructure. | ||
| 4. | Results | Penetration Testing | A proof of concept for every exploited vulnerability, a narrative of the attack path, and a thorough evaluation of the business risk are all included in the qualitative report. |
| Vulnerability Scanning | The quantitative report offers a list of vulnerabilities that have been found, together with repair recommendations and severity levels (such as low, medium, and high). | ||
| 5. | Cost & Frequency | Penetration Testing | Because it is more costly and time-consuming, it is often carried out on essential systems less regularly (e.g., once a year or following significant changes). |
| Vulnerability Scanning | Because of its speed and lower cost, it can be used often (monthly, even daily) to offer ongoing monitoring. |

You can choose the right penetration testing provider for your business in the following ways:
Now that we have talked about “Application Penetration Testing Services,” you might be wondering where you could get the best experience for such services. For that, Craw Security is the suitable one for you.
Craw Security has been offering the Application Penetration Testing Service in Singapore to various organizations for securing their working infrastructure against online threats. What are you waiting for? Contact, Now!
1. What is Application Penetration Testing, and why is it important?
Application penetration testing is crucial because it offers a realistic evaluation of an application’s defenses before an actual attacker can cause a breach. It involves a manual, simulated cyberattack on an application to identify and exploit security flaws.
2. How can professional penetration testing help protect my business?
Professional penetration testing helps protect your business in the following ways:
3. What are the key benefits of hiring an expert penetration testing service?
The following are the key benefits of hiring an expert penetration testing service:
4. How do penetration testers identify security vulnerabilities in applications?
Penetration testers can identify security vulnerabilities in applications in the following ways:
5. What is the difference between penetration testing and vulnerability scanning?
While penetration testing is a manual procedure that actively exploits those vulnerabilities to mimic a real-world attack and assess the company’s effect, vulnerability scanning is an automated method that finds known vulnerabilities.
6. How often should my organization conduct application penetration tests?
An enterprise should, at the very least, do application penetration tests once a year or following any major modifications to the features, infrastructure, or code of the application.
7. Can penetration testing help with regulatory compliance and industry standards?
Because penetration testing offers verified proof that a company has proactively found and fixed security flaws, it is, in fact, an essential component of adhering to industry standards and regulatory compliance.
8. What are the potential risks if I don’t perform regular penetration testing?
Following are some potential risks if you don’t perform regular penetration testing:
9. How long does a typical application penetration test take?
Depending on the complexity, size, number of user roles, and scope of the application, a typical application penetration test can take anywhere from one to four weeks; however, this can vary greatly.
10. hat should I expect during an application penetration test?
A systematic, multi-phase approach comprising planning, vulnerability scanning, ethical hacker manual exploitation, and a comprehensive final report with practical suggestions is what to anticipate from an application penetration test.
11. What should I look for when choosing a professional penetration testing provider?
You should look for the following things while choosing a professional penetration testing provider:
12. How much does professional application penetration testing cost?
Depending on variables including the application’s size, complexity, and test scope, professional application penetration testing in Singapore can cost anywhere from a few thousand to tens of thousands of Singapore dollars.
13. Can penetration testing prevent data breaches and hacking attempts?
By proactively finding and addressing exploitable vulnerabilities before attackers can discover and take advantage of them, penetration testing considerably lowers the chance and effect of data breaches and hacking attempts, although it cannot ensure that all of them will be prevented.
14. What happens after a penetration test is completed?
The following things happen after a penetration test is completed:
15. Are the results of a penetration test confidential?
Yes, a penetration test’s findings are regarded as extremely private and ought to be handled as sensitive corporate data.